15 Jun No point in paying ransomware, increases likelihood for second attack
Some believe paying ransomware gangs is a “fix,” but results say otherwise
“Don’t negotiate” with ransomware gangs is becoming a fast and hard rule in the cybersecurity world. The idea is simple: don’t pay threat actors who deploy ransomware, because doing so only encourages their activity. Makes sense, they’ll keep doing something making them a profit.
But in a tough situation, victims of ransomware attacks feel they’re left without a choice. If they don’t, attackers publish and/or destroy the information they’ve stolen. We don’t just mean enterprise data, either, this can range from info like credit card details to personal data hijacked from a hospital network. Because of how precious said information is, decisions are exceedingly difficult to make. Many have to put their customer data first, which is admirable.
Though, experts are finding this isn’t helping, and won’t help either the company or people in the long term. Sounds like a broken record, doesn’t it? “Ransomware is a threat, what else is new!”
But it’s a reality we need to confront, because we’re in it for the long haul unless there are wide, systemic changes.
Why paying ransomware isn’t a true solution
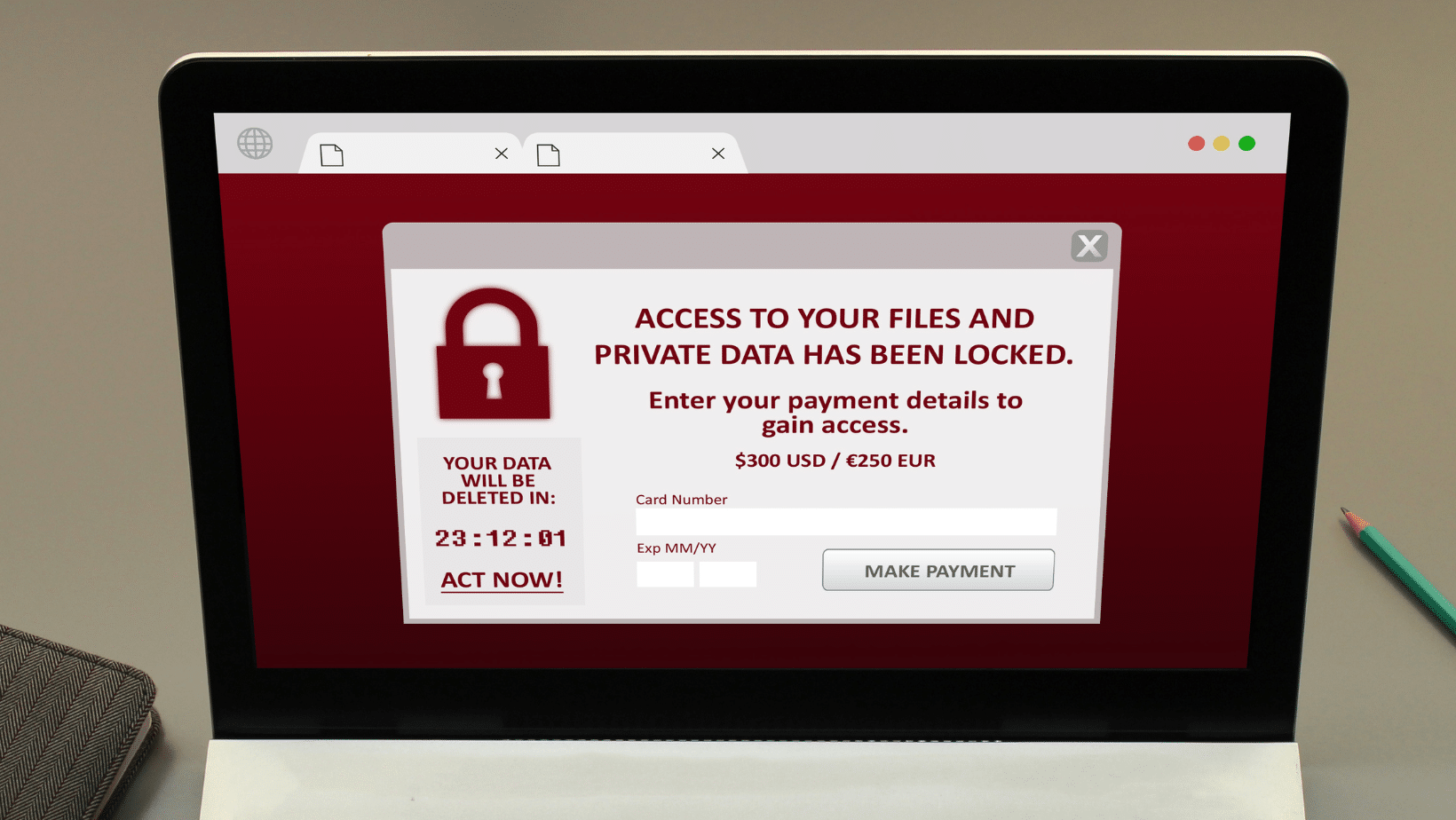
In the victim’s scenario, all systems and files are arrested by a malicious file until the ransom(s) is paid to the attacker. If the ransom is paid, the offending party promises to remove the encryption and return access to all files.
It’s an ugly scenario for anyone involved. Ransomware attacks stretch far, from single-person hits to entire business networks. But, once the ransom is paid, it’s at least over, right? Unfortunately, attackers have shown they’re more than willing to go after the same target(s) again. In those cases, they’re referred to as “double extortion” attacks, which is exactly as it sounds. Victims are confronted with the same ransomware schemes, months after the first ransomware attack.
Even if they paid the first time, it does not deter attacks. It’s why the CISA and FBI heavily discourage any payment to threat actors in a ransomware breach event. For the reasons above, but also because paying a threat actor relies entirely on an “honor” system. We are to seriously believe that hackers, who already engaged in malign activity for profit, won’t try it again if given the opportunity? Because they said they wouldn’t?
I can’t say what I want for professional reasons, but I can say that’s BS, a bologna sandwich.
“No honor among thieves,” the phrase is, and that’s true enough here. You can’t trust malicious gangs to make a good faith argument that they’ll leave you alone.
The FBI lays out the consequences for paying a ransomware gang in the event of a breach:
- Return of data is never guaranteed
- Data can be damaged during decryption/return of data
- Once again, threat actors are not obliged to honor their “promise”
- Encourages further ransomware attacks against the same victim or new ones
However, even with these tradeoffs, many feel they have no choice but to pay up. In the event they do not, ransomware attacks try extortion attacks, as I’ve mentioned. That ranges from publishing the data, selling it to dark web markets (which creates more threat campaigns), and/or outright destroying the information.
But, remember, while paying the attackers seems like a fix, given they attack more than once, and demand higher payments the second time, giving in is an unwise idea.
It’s an incredibly difficult decision.
The reality is the best way to avoid these scenarios is to do that: avoid them. It pays, literally, to have good cybersecurity policies and training for ransomware situations.
For more information about dealing with ransomware, contact Bytagig today.
Share this post:

Sorry, the comment form is closed at this time.